

CentOS7にWordPressをインストールし、Let's EncryptでSSL対応したメモです。
WordPressはこのサイトでも利用しているCMSです。今回はCentOS7にWordPressをインストールし、無料で取得が出来るSSL証明書(DV)も併せて設定します。
利用OS
CentOS Linux release 7.4.1708 Minimal
設定サイト
test.server-network-note.net
※設定中は上記自分のサイトに読み替えて設定して下さい。
CentOS7をダウンロード https://www.centos.org/download/ から Mnimal ISOをダウンロード
CentOS7 のインストールは省略
selinuxの無効化 と パッケージの最新化
/etc/selinux/config の SELINUX=enforcing → SELINUX=disabled に変更
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
[root@test ~]# cat /etc/selinux/config # This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - No SELinux policy is loaded. SELINUX=disabled # SELINUXTYPE= can take one of three two values: # targeted - Targeted processes are protected, # minimum - Modification of targeted policy. Only selected processes are protected. # mls - Multi Level Security protection. SELINUXTYPE=targeted [root@test ~]# |
パッケージを最新に更新
|
1 |
[root@test ~]# yum update -y |
再起動
|
1 |
[root@test ~]# reboot |
Apache/mod_ssl/php/MariaDB インストール
パッケージをインストール
|
1 |
[root@test ~]# yum -y install httpd php php-mysql php-mbstring mod_ssl mariadb mariadb-server |
phpのタイムゾーンを変更
|
1 2 3 4 5 |
[Date] ; Defines the default timezone used by the date functions ; http://php.net/date.timezone ;date.timezone = date.timezone = "Asia/Tokyo" |
/etc/php.ini の date.timezone を 修正
MariaDB の文字コードを utf-8 に変更
|
1 2 |
[client] default-character-set = utf8 |
/etc/my.cnf.d/client.cnf に上記を追加
|
1 2 |
[mysqld] character-set-server = utf8 |
/etc/my.cnf.d/server.cnf [mysqld]の設定項目にcharacter-set-server = utf8を追加
MariaDB 起動 WordPress用のdatabaseを作成
MariaDB起動
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
[root@test ~]# systemctl start mariadb.service [root@test ~]# systemctl status mariadb.service ● mariadb.service - MariaDB database server Loaded: loaded (/usr/lib/systemd/system/mariadb.service; disabled; vendor preset: disabled) Active: active (running) since 金 2017-11-03 19:02:44 JST; 13s ago Process: 1376 ExecStartPost=/usr/libexec/mariadb-wait-ready $MAINPID (code=exited, status=0/SUCCESS) Process: 1296 ExecStartPre=/usr/libexec/mariadb-prepare-db-dir %n (code=exited, status=0/SUCCESS) Main PID: 1375 (mysqld_safe) CGroup: /system.slice/mariadb.service ├─1375 /bin/sh /usr/bin/mysqld_safe --basedir=/usr └─1549 /usr/libexec/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib64/mysql/plugin --log-er... 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: MySQL manual for more instructions. 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: Please report any problems at http://mariadb....ira 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: The latest information about MariaDB is avail...g/. 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: You can find additional information about the...at: 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: http://dev.mysql.com 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: Consider joining MariaDB's strong and vibrant...ty: 11月 03 19:02:42 test.localhost.localdomain mariadb-prepare-db-dir[1296]: https://mariadb.org/get-involved/ 11月 03 19:02:42 test.localhost.localdomain mysqld_safe[1375]: 171103 19:02:42 mysqld_safe Logging to '/var/log/mariad...og'. 11月 03 19:02:42 test.localhost.localdomain mysqld_safe[1375]: 171103 19:02:42 mysqld_safe Starting mysqld daemon with...ysql 11月 03 19:02:44 test.localhost.localdomain systemd[1]: Started MariaDB database server. Hint: Some lines were ellipsized, use -l to show in full. [root@test ~]# |
Statusが Active: active (running) が出ていたら起動成功
MariaDBの自動起動を設定
|
1 2 3 4 5 6 7 |
[root@test ~]# systemctl is-enabled mariadb.service disabled [root@test ~]# systemctl enable mariadb.service Created symlink from /etc/systemd/system/multi-user.target.wants/mariadb.service to /usr/lib/systemd/system/mariadb.service. [root@test ~]# systemctl is-enabled mariadb.service enabled [root@test ~]# |
MariaDBのインストール
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 |
[root@test ~]# /usr/bin/mysql_secure_installation NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY! In order to log into MariaDB to secure it, we'll need the current password for the root user. If you've just installed MariaDB, and you haven't set the root password yet, the password will be blank, so you should just press enter here. Enter current password for root (enter for none): OK, successfully used password, moving on... Setting the root password ensures that nobody can log into the MariaDB root user without the proper authorisation. Set root password? [Y/n] y New password: Re-enter new password: Password updated successfully! Reloading privilege tables.. ... Success! By default, a MariaDB installation has an anonymous user, allowing anyone to log into MariaDB without having to have a user account created for them. This is intended only for testing, and to make the installation go a bit smoother. You should remove them before moving into a production environment. Remove anonymous users? [Y/n] y ... Success! Normally, root should only be allowed to connect from 'localhost'. This ensures that someone cannot guess at the root password from the network. Disallow root login remotely? [Y/n] y ... Success! By default, MariaDB comes with a database named 'test' that anyone can access. This is also intended only for testing, and should be removed before moving into a production environment. Remove test database and access to it? [Y/n] y - Dropping test database... ... Success! - Removing privileges on test database... ... Success! Reloading the privilege tables will ensure that all changes made so far will take effect immediately. Reload privilege tables now? [Y/n] y ... Success! Cleaning up... All done! If you've completed all of the above steps, your MariaDB installation should now be secure. Thanks for using MariaDB! [root@test ~]# |
Passwordを設定しますが、MariaDBのrootパスワードになります。後ほど利用します。
WordPress用のDBとDB接続用のユーザを作成します。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
[root@test ~]# mysql -u root -p Enter password: Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 10 Server version: 5.5.56-MariaDB MariaDB Server Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MariaDB [(none)]> CREATE DATABASE wordpress_db; Query OK, 1 row affected (0.00 sec) MariaDB [(none)]> GRANT ALL PRIVILEGES ON wordpress_db .* TO "wordpress_user"@"localhost" IDENTIFIED BY "wordpress_password"; Query OK, 0 rows affected (0.00 sec) MariaDB [(none)]> FLUSH PRIVILEGES; Query OK, 0 rows affected (0.00 sec) MariaDB [(none)]> EXIT Bye [root@test ~]# |
コマンド実行時にパスワードが聞かれますが、先ほど設定したMariaDBのパスワードを入力すると接続できます。
今回のDBやDB用のユーザおよびパスワードはwordpress_* で設定していますので、任意に変更して下さい。パスワードなどは複雑な文字列を推奨します。
WordPressインストールおよびApache設定
/var/www/html 配下に最新の WordPress 日本語版をダウンロードします。
|
1 2 3 4 5 6 7 8 9 |
[root@test ~]# cd /var/www/html/ [root@test html]# pwd /var/www/html [root@test html]# curl -LO http://ja.wordpress.org/latest-ja.tar.gz % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 178 100 178 0 0 359 0 --:--:-- --:--:-- --:--:-- 359 100 8465k 100 8465k 0 0 77689 0 0:01:51 0:01:51 --:--:-- 121k [root@test html]# |
ダウンロードしたファイルを解凍、展開します。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
[root@test html]# tar xvzf latest-ja.tar.gz wordpress/ wordpress/wp-mail.php wordpress/xmlrpc.php wordpress/wp-trackback.php wordpress/wp-load.php / snip / wordpress/wp-signup.php wordpress/readme.html wordpress/wp-config-sample.php wordpress/wp-blog-header.php wordpress/wp-links-opml.php [root@test html]# |
WordPressの設定ファイルを編集します。(sampleをコピーして編集します。)
ファイルは先ほど設定したデータベースの設定に併せて変更します。
|
1 2 3 4 5 6 7 8 9 10 11 |
[root@test html]# cp wordpress/wp-config-sample.php wordpress/wp-config.php [root@test html]# vi wordpress/wp-config // ** MySQL 設定 - この情報はホスティング先から入手してください。 ** // /** WordPress のためのデータベース名 */ define('DB_NAME', 'wordpress_db'); /** MySQL データベースのユーザー名 */ define('DB_USER', 'wordpress_user'); /** MySQL データベースのパスワード */ define('DB_PASSWORD', 'wordpress_password'); |
インストールしたWordPressのファイルをApacheユーザへ変更
|
1 |
[root@test html]# chown -R apache:apache /var/www/html/wordpress |
Apacheの環境設定
/etc/httpd/conf/httpd.conf を下記に編集
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
#サーバ名を変更 #ServerName www.example.com:80 ServerName test.server-network-note.net:80 #DocumentRoot "/var/www/html" DocumentRoot "/var/www/html/wordpress" #<Directory "/var/www/html"> <Directory "/var/www/html/wordpress"> # <Directory "/var/www/html/wordpress"> 下の AllowOverride を書き換える #AllowOverride None AllowOverride All # DirectoryIndex に index.php を追加 <IfModule dir_module> #DirectoryIndex index.html DirectoryIndex index.html index.php </IfModule> |
Apache起動
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
[root@test ~]# systemctl start httpd [root@test ~]# systemctl status httpd ● httpd.service - The Apache HTTP Server Loaded: loaded (/usr/lib/systemd/system/httpd.service; disabled; vendor preset: disabled) Active: active (running) since 金 2017-11-03 20:32:59 JST; 5s ago Docs: man:httpd(8) man:apachectl(8) Main PID: 11210 (httpd) Status: "Processing requests..." CGroup: /system.slice/httpd.service ├─11210 /usr/sbin/httpd -DFOREGROUND ├─11212 /usr/sbin/httpd -DFOREGROUND ├─11213 /usr/sbin/httpd -DFOREGROUND ├─11214 /usr/sbin/httpd -DFOREGROUND ├─11215 /usr/sbin/httpd -DFOREGROUND └─11216 /usr/sbin/httpd -DFOREGROUND 11月 03 20:32:59 test.localhost.localdomain systemd[1]: Starting The Apache HTTP Server... 11月 03 20:32:59 test.localhost.localdomain systemd[1]: Started The Apache HTTP Server. [root@test ~]# |
Statusが Active: active (running) が出ていたら起動成功
|
1 2 3 4 5 6 7 |
[root@test ~]# systemctl is-enabled httpd disabled [root@test ~]# systemctl enable httpd Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service. [root@test ~]# systemctl is-enabled httpd enabled [root@test ~]# |
enabledが表示されていたら自動起動設定OK
firewallの設定
|
1 2 3 4 5 6 7 8 9 |
[root@test ~]# firewall-cmd --list-services ssh dhcpv6-client [root@test ~]# firewall-cmd --add-service=http --permanent success [root@test ~]# firewall-cmd --reload success [root@test ~]# firewall-cmd --list-services ssh dhcpv6-client http [root@test ~]# |
http(80)を追加します。 --list-services にhttpが追加されていたら設定完了です。
ブラウザから http://test.server-network-note.net/ へ接続
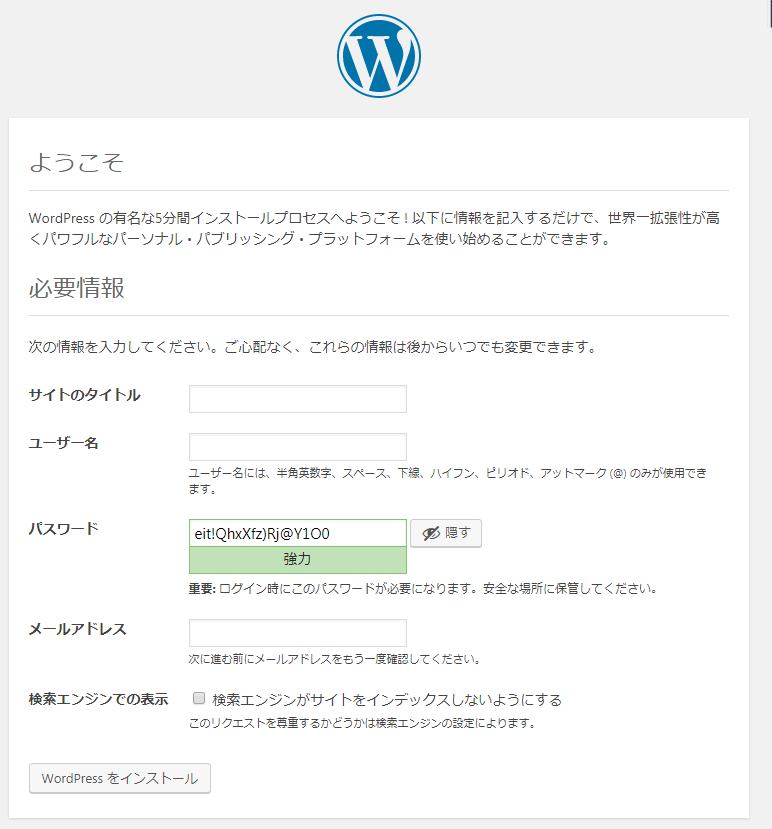
接続が出来たら WordPressのインストールは成功です。
Let's Encrypt のインストール
Let's Encryptとは無料のSSL証明書を発行するサービスです。詳細は下記サイトをどうぞ。
https://letsencrypt.jp/
Let's Encryptをインストールします。
|
1 2 |
[root@test ~]# yum -y install epel-release [root@test ~]# yum -y install certbot python-certbot-apache |
各コマンドで完了しました!が出ていたらインストール完了です。
証明書の作成
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
[root@test ~]# certbot certonly --webroot -w /var/www/html/wordpress/ -d test.server-network-note.net Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator webroot, Installer None Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): test@server-network-note.net Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org ------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- (A)gree/(C)ancel: A ------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about EFF and our work to encrypt the web, protect its users and defend digital rights. ------------------------------------------------------------------------------- (Y)es/(N)o: N Obtaining a new certificate Performing the following challenges: http-01 challenge for test.server-network-note.net Using the webroot path /var/www/html/wordpress for all unmatched domains. Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/test.server-network-note.net/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/test.server-network-note.net/privkey.pem Your cert will expire on 2018-02-01. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le [root@test ~]# |
1回目の問い合わせにメールアドレスを入力 2回目は利用規約同意でY 3回目はLet's Encryptプロジェクトにメールアドレスを共用するか問い合わせなのでN (Yでも問題ないです)
作成された証明書は下記に保存されています。
|
1 2 3 4 5 6 7 8 |
[root@test ~]# find /etc/letsencrypt/live/test.server-network-note.net/ /etc/letsencrypt/live/test.server-network-note.net/ /etc/letsencrypt/live/test.server-network-note.net/cert.pem /etc/letsencrypt/live/test.server-network-note.net/privkey.pem /etc/letsencrypt/live/test.server-network-note.net/chain.pem /etc/letsencrypt/live/test.server-network-note.net/fullchain.pem /etc/letsencrypt/live/test.server-network-note.net/README [root@test ~]# |
/etc/httpd/conf.d/ssl.conf を下記のように変更します。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
# Server Certificate: # Point SSLCertificateFile at a PEM encoded certificate. If # the certificate is encrypted, then you will be prompted for a # pass phrase. Note that a kill -HUP will prompt again. A new # certificate can be generated using the genkey(1) command. #SSLCertificateFile /etc/pki/tls/certs/localhost.crt SSLCertificateFile /etc/letsencrypt/live/test.server-network-note.net/cert.pem # Server Private Key: # If the key is not combined with the certificate, use this # directive to point at the key file. Keep in mind that if # you've both a RSA and a DSA private key you can configure # both in parallel (to also allow the use of DSA ciphers, etc.) #SSLCertificateKeyFile /etc/pki/tls/private/localhost.key SSLCertificateKeyFile /etc/letsencrypt/live/test.server-network-note.net/privkey.pem # Server Certificate Chain: # Point SSLCertificateChainFile at a file containing the # concatenation of PEM encoded CA certificates which form the # certificate chain for the server certificate. Alternatively # the referenced file can be the same as SSLCertificateFile # when the CA certificates are directly appended to the server # certificate for convinience. #SSLCertificateChainFile /etc/pki/tls/certs/server-chain.crt SSLCertificateChainFile /etc/letsencrypt/live/test.server-network-note.net/chain.pem |
続いて設定した証明書を反映させる為にApacheを再起動し、ファイアウォールにhttps(443)を追加します。
|
1 2 3 4 5 6 7 |
[root@test conf.d]# systemctl restart httpd [root@test conf.d]# [root@test conf.d]# firewall-cmd --add-service=https --permanent success [root@test conf.d]# firewall-cmd --reload success [root@test conf.d]# |
設定が完了しました。 ブラウザで https://test.server-network.net/ にアクセスしてみましょう。
![]()
Chrome の場合 https で正しい証明書が作成されていたら、上のように「保護された通信」が表示されます。
SSL証明書の更新
Let'sEncryptで取得した証明書の期限は3ヶ月になります。それまでに更新する必要があります。
crontab で毎週水曜日 3時15分に更新する設定を入れます。
|
1 2 3 4 |
[root@test ~]# crontab -e -u root # Let's Encrypt Renew 15 3 * * 4 /bin/certbot renew --webroot -w /var/www/html/wordpress/ --post-hook "/bin/systemctl reload httpd.service" [root@test ~]# |
毎週チェックは実施しますが、実際の更新は期限が切れる30日前にならないと更新されません。強制的に更新するにはオプションとして --force-renewal が必要になります。crontab に設定される前に実際に更新出来るかテストをお勧めします。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
[root@test ~]# /bin/certbot renew --force-renewal --webroot -w /var/www/html/wordpress/ --post-hook "/bin/systemctl reload httpd.service" Saving debug log to /var/log/letsencrypt/letsencrypt.log ------------------------------------------------------------------------------- Processing /etc/letsencrypt/renewal/test.server-network-note.net.conf ------------------------------------------------------------------------------- Plugins selected: Authenticator webroot, Installer None Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org Renewing an existing certificate Performing the following challenges: http-01 challenge for test.server-network-note.net Using the webroot path /var/www/html/wordpress for all unmatched domains. Waiting for verification... Cleaning up challenges ------------------------------------------------------------------------------- new certificate deployed without reload, fullchain is /etc/letsencrypt/live/test.server-network-note.net/fullchain.pem ------------------------------------------------------------------------------- ------------------------------------------------------------------------------- Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/test.server-network-note.net/fullchain.pem (success) ------------------------------------------------------------------------------- Running post-hook command: /bin/systemctl reload httpd.service [root@test ~]# |
上記が --force-renewal を入れて実効した結果です。Congratulations, all renewals succeeded.が出ていたら更新に成功です。
設定は以上です。SSL証明書が無料で取得し更新は自動です。非常に便利です。よかったら皆さんも設定して見て下さい。